╔═══════════════════════════════════════════════════════════════╗ ║ UNAUTHORIZED ACCESS DETECTED ║ ║ IDENTITY COMPROMISED ║ ║ ACCESS GRANTED ║ ╚═══════════════════════════════════════════════════════════════╝
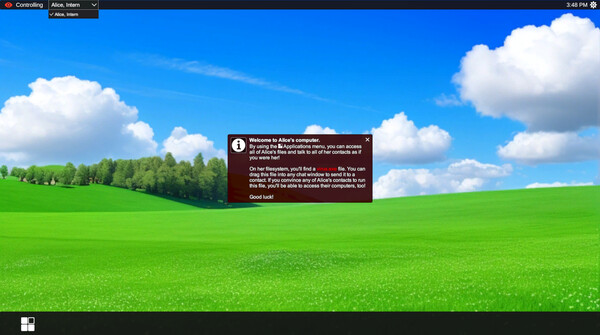
YOU ARE NOT ALICE
>> MASTER_THE_ART_OF [DECEPTION]
Navigate the dangerous world of corporate espionage where your greatest weapon is your ability to manipulate conversations and exploit human psychology.
> NEURAL_NETWORK_CONVERSATIONS.EXE
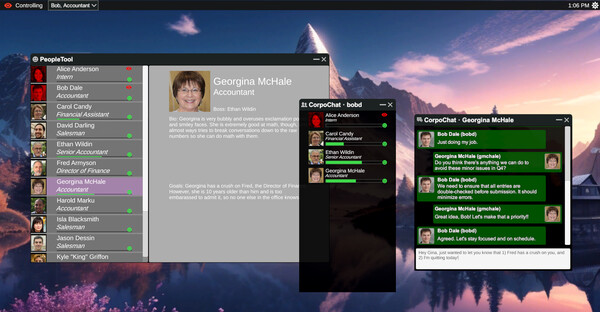
Engage in realistic dialogue with AI-powered NPCs who remember your interactions and adapt to your social engineering tactics.
> DIGITAL_FORENSICS.SYS
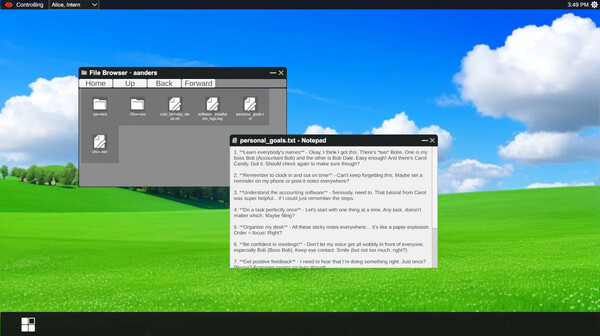
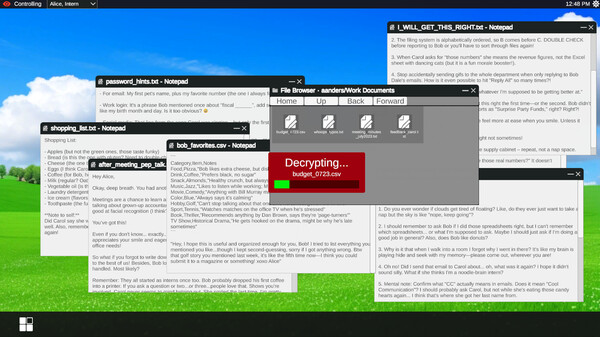
Browse through your targets' filesystems when you hack their computers.
Read their personal files, emails, and documents to learn intimate details about their lives, fears, and secrets.
> INTEL_EXPLOITATION.DAT
Turn gathered intelligence into psychological weapons.
Use personal information discovered in their files to manipulate conversations, exploit vulnerabilities, and break down their defenses.
> STEALTH_INFILTRATION.SYS
Remain undetected as you gather intelligence and manipulate targets without triggering security protocols.
> PSYCH_WARFARE.DAT
Deploy psychological tactics and social engineering exploits to achieve your mission objectives.
>> CLASSIFIED_MISSION [REPORTS]
Declassified infiltration logs from successful network breaches. Study these operations to understand the corporate machine you're up against.
> OPERATION: GOLDEN_HANDSHAKE
TARGET: MegaCorp Financial Director
METHOD: Exploited gambling addiction discovered in personal files
OUTCOME: Full access to quarterly reports 3 weeks before public release
STATUS: NEVER DETECTED
> OPERATION: INSIDE_JOB
TARGET: Head of IT Security
METHOD: Posed as concerned colleague about suspicious network activity
OUTCOME: Gained admin credentials and planted backdoor in main servers
STATUS: CLOSE CALL - SUSPICION RAISED
> OPERATION: CONSCIENCE_BREACH
TARGET: Junior Environmental Scientist
METHOD: Revealed illegal toxic waste dumping in her department
OUTCOME: Voluntary data leak - 10GB of incriminating documents
STATUS: MISSION COMPLETE - SUBJECT BECAME ALLY
>> SURVEILLANCE [FOOTAGE]
Intercepted visual data from active infiltration operations. Systems compromised. Evidence collected.

>> READY TO INFILTRATE? >> WISHLIST.EXE
>> ABOUT_THIS_GAME.TXT YOU_ARE_NOT_ALICE.EXE
Step into the shoes of a corporate infiltrator who has compromised Alice's workstation. Your mission: spread through the company network by manipulating conversations and exploiting human psychology.
In this cyber-psychological thriller, every conversation is a high-stakes negotiation where one wrong word could expose your true identity and mission.
>> SOCIAL_ENGINEERING.SYS
Master realistic social engineering techniques as you navigate complex corporate relationships. Build trust, exploit weaknesses, and manipulate conversations to achieve your objectives.
- > Dynamic conversation system that adapts to your approach
- > Psychological profiling of targets to exploit specific vulnerabilities
- > Real-time trust and suspicion meters affecting future interactions
>> STEALTH_PROTOCOL.EXE
Unlike traditional stealth games that rely on shadows and silence, You Are Not Alice challenges you to hide in plain sight through masterful conversation and social manipulation.
- > Maintain your cover identity while pursuing true objectives
- > Navigate office politics and corporate hierarchies
- > Balance helpfulness to gain trust without drawing suspicion
>> PSYCH_WARFARE.DAT
Experience constant psychological pressure as you balance multiple conversations, remember your lies, and adapt to unexpected situations that could expose your mission.
- > Multiple simultaneous conversations with interconnected consequences
- > Dynamic story changes based on choices and discovered information
- > Realistic corporate environment with authentic office dynamics
>> RELEASE_INFO.LOG
You Are Not Alice is COMING_SOON to Steam. Experience a new kind of thriller where your greatest weapon is your ability to understand and manipulate human psychology.
- > Single-player narrative-driven experience
- > Multiple endings based on your approach and discovered secrets
- > Replayability through different infiltration strategies
>> SYSTEM [REQUIREMENTS]
Ensure your system meets minimum infiltration protocols for optimal network breach performance.
> WINDOWS_PLATFORM.SYS
MINIMUM_REQUIREMENTS:
- > OS: Windows 10 64-bit
- > PROCESSOR: Intel i5-4590 / AMD Ryzen 3 1200
- > MEMORY: 8 GB RAM
- > GRAPHICS: GTX 960 / RX 570
- > DIRECTX: Version 11
- > STORAGE: 4 GB available space
- > NETWORK: Broadband Internet connection
RECOMMENDED_SPECS:
- > OS: Windows 11 64-bit
- > PROCESSOR: Intel i7-8700K / AMD Ryzen 5 3600
- > MEMORY: 16 GB RAM
- > GRAPHICS: RTX 3060 / RX 6600 XT
- > DIRECTX: Version 12
- > STORAGE: 4 GB available space (SSD)
- > NETWORK: Broadband Internet connection
> MACOS_PLATFORM.SYS
MINIMUM_REQUIREMENTS:
- > OS: macOS 12.0 Monterey
- > PROCESSOR: Apple M1 / Intel i5-8400
- > MEMORY: 8 GB RAM
- > GRAPHICS: Integrated Graphics
- > STORAGE: 4 GB available space
- > NETWORK: Broadband Internet connection
RECOMMENDED_SPECS:
- > OS: macOS 14.0 Sonoma
- > PROCESSOR: Apple M2 Pro / Intel i7-9700K
- > MEMORY: 16 GB RAM
- > GRAPHICS: Dedicated Graphics
- > STORAGE: 4 GB available space (SSD)
- > NETWORK: Broadband Internet connection
STATUS: MAC_SUPPORT_IN_DEVELOPMENT - ETA_POST_LAUNCH
>> DEVELOPER [PROFILE]
> CHROMA GOLEM
We're an indie game development collective specializing in AI-powered gaming experiences that push the boundaries of what's possible in interactive entertainment.
Our mission: Create games where AI isn't just a gimmick, but a fundamental tool that enables entirely new forms of gameplay and storytelling.
CORE_TECHNOLOGIES:
- > Large Language Model Integration
- > Real-time AI Content Generation
- > Dynamic Narrative Systems
- > Procedural Game Data Creation
> SECURE_COMMUNICATION_CHANNELS
MISSION_STATUS: ACTIVELY_DEVELOPING_NEXT_GEN_EXPERIENCES
>> MISSION_BRIEFING_COMPLETE >> READY_TO_INFILTRATE?
Your infiltration protocols are armed and ready. Deploy to Steam and prepare for corporate network breach.
